Azure Application Gateway is a web traffic load balance that provides application layer (OSI level 7) load balancing, and includes the Web Application Firewall (WAF). The Application Gateway offers a scalable service that is fully managed by Azure.Its main goal is to protect a web application to common attack like SQL injections, cross-site scripting.
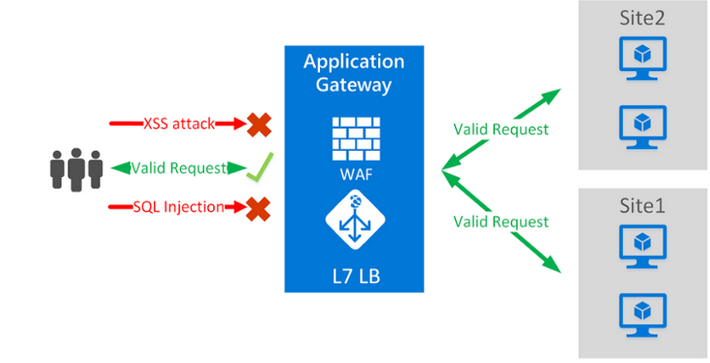
Source : Microsoft
Features
- SQL-injection protection.
- Cross-site scripting protection.
- Protection against other common web attacks, such as command injection, HTTP request smuggling, HTTP response splitting, and remote file inclusion.
- Protection against HTTP protocol violations.
- Protection against HTTP protocol anomalies, such as missing host user-agent and accept headers.
- Protection against crawlers and scanners.
- Detection of common application misconfigurations (for example, Apache and IIS).
- Configurable request size limits with lower and upper bounds.
- Exclusion lists let you omit certain request attributes from a WAF evaluation. A common example is Active Directory-inserted tokens that are used for authentication or password fields.
- Create custom rules to suit the specific needs of your applications.
- Geo-filter traffic to allow or block certain countries/regions from gaining access to your applications. (preview)
- Protect your applications from bots with the bot mitigation ruleset. (preview)
- Inspect JSON and XML in the request body
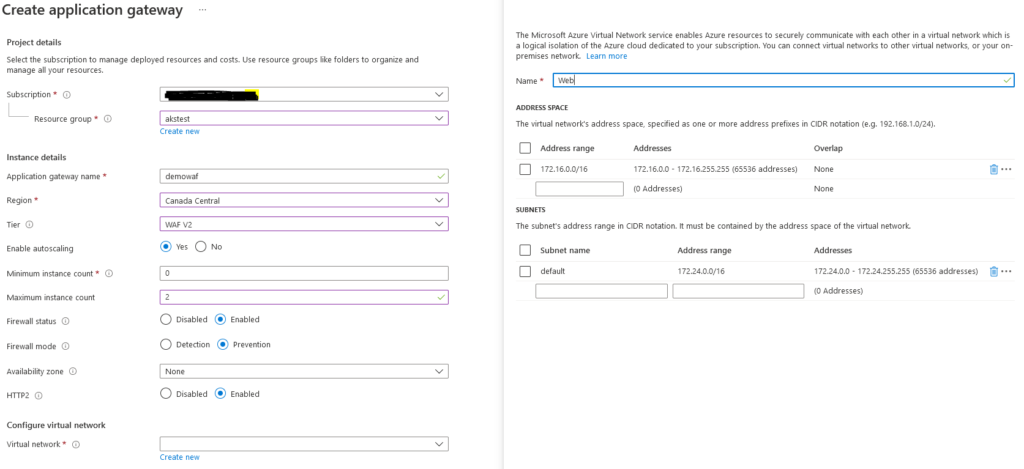
Step 1:
Login to Azure portal. Select Application gateway and create
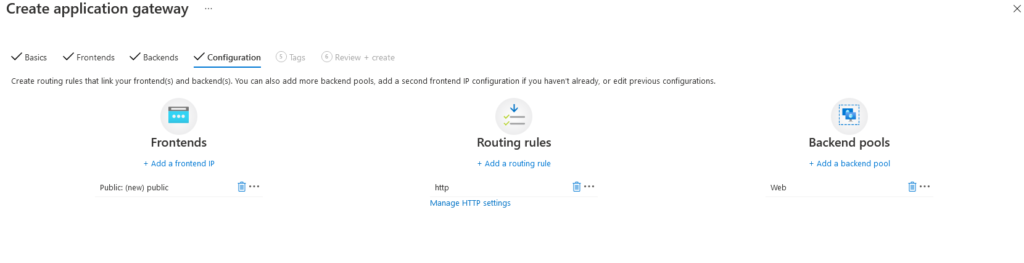
Added Frontend, backend pool and routing rules.
WAF modes
The Application Gateway WAF can be configured to run in the following two modes:
- Detection mode: Monitors and logs all threat alerts. You turn on logging diagnostics for Application Gateway in the Diagnostics section. You must also make sure that the WAF log is selected and turned on. Web application firewall doesn’t block incoming requests when it’s operating in Detection mode.
- Prevention mode: Blocks intrusions and attacks that the rules detect. The attacker receives a “403 unauthorized access” exception, and the connection is closed. Prevention mode records such attacks in the WAF logs.
Below Screenshot explains how to configure each component in WAF.

